Verifiable Computation
In page of "Verifiable computing" of wikipedia, Verifiable computing (or verified computation or verified computing) enables a computer to offload the computation of some function, to other perhaps untrusted clients, while maintaining verifiable results. The other clients evaluate the function and return the result with a proof that the computation of the function was carried out correctly. The introduction of this notion came as a result of the increasingly common phenomenon of "outsourcing" computation to untrusted users in projects such as SETI@home and also to the growing desire of weak clients to outsource computational tasks to a more powerful computation service like in cloud computing.
What is the NIZK?
Interactive Proofs (IPs) and ArgumentsProver P and Verfier V
1. P solves a problem on a given input.
2. Tells V the answer.
3. Then P proves to V that the answer is correct.Requirements:
Completeness: If the answer is true, the honest V will be convinced of this fact by an untrusted P (honest P in ZKP).
Soundness: If the answer is false, no P (no cheating P in ZKP) can convince the honest V that it is true, except with some small probability.
Difference of IPs and Arguments
The difference is that the prover is restricted to be a polynomial-time algorithm for an interactive arguement, whereas no such restrictions on the prover apply for an interactive proof.
Zero-Knowledge Proof
ZKP is one of the IPs and is a method by which P can prove to V that they know a secret, without conveying any information apart from the fact that they know the secret.More requirement for ZKP:
Zero-knowledge: If the answer is true, no V learns anything other than the fact that the answer is true.
Non-Interactive Proofs
Non-Interactive Proofs require no interaction between the P and V.
What is the PCD?
Proof-carrying data, PCD, is a cryptographic primitive applied to distributed computing, in DAG(directed acyclic graph), where multiple subjects without mutual trust generally participate.
In distributed computing, when a large operation is performed in multiple steps, the subject, in each node in distributed computing, of a step in the operation sends message including result of the operation to the subject who performs the next step of operation.
A proof is attached to the message, and the proof attests about the correctness of the result of the operation performed at both of present node and previous one.
However, depending on the time complexity of the operation of the verifier algorithm, the size of the proof grows larger as the operation proceeds, so verifying the proof requires more computation than performing the operation directly, so the verification becomes meaningless.
So, research on the types of proof systems that can be used as a component of the recursive proof composition and the method of the recursive proof composition is ongoing.
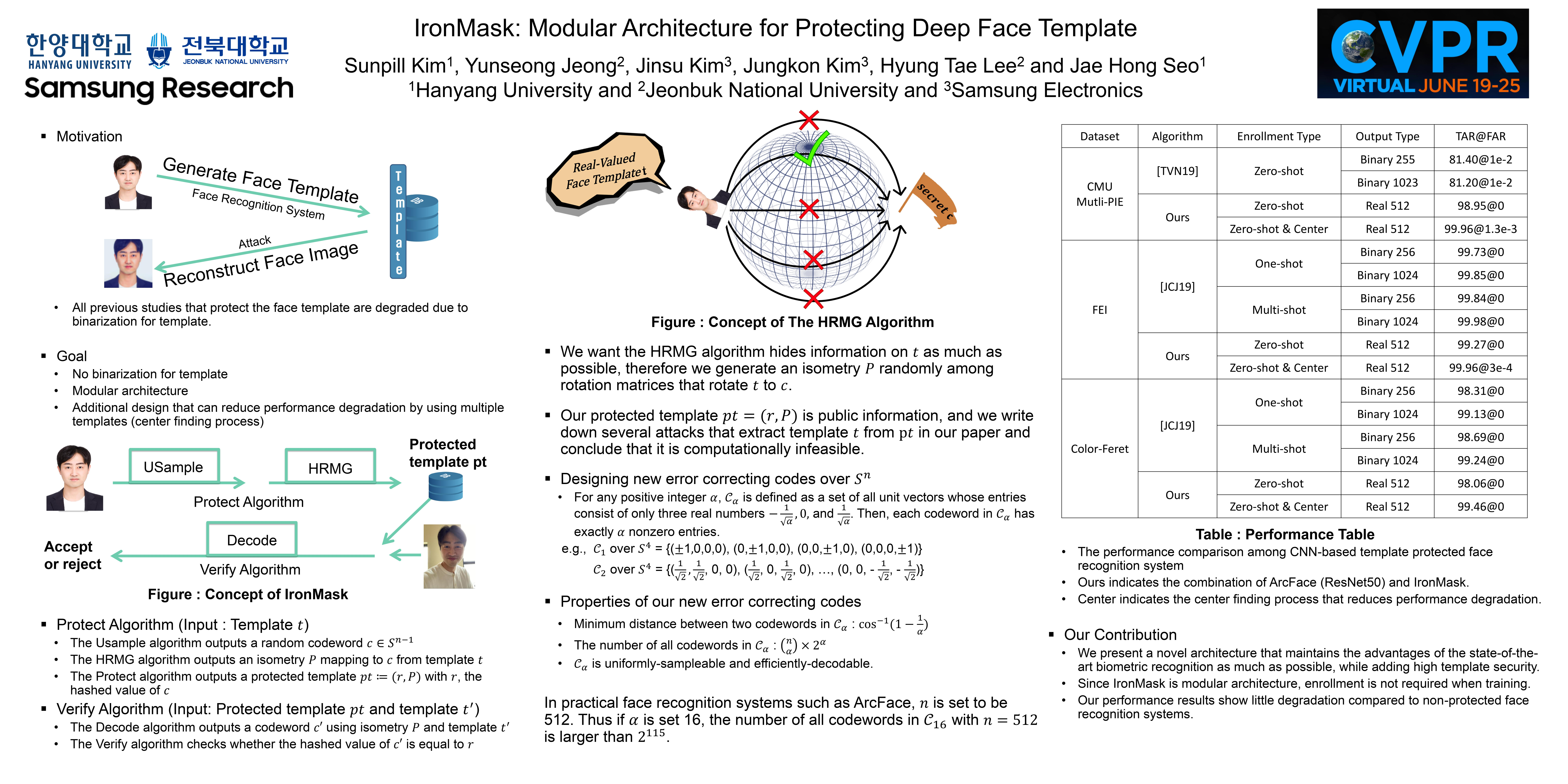
Secure Machine Learning (Cryptographic Approach)
With the successful development of deep learning, biometric authentication technology based on convolutional neural networks has remarkably advanced.
ArcFace based on Residual neural network, one of the convolutional neural networks, is the recent state-of-the-art face recognition system and outputs highly discriminative feature templates for face authentication using additive angular margin loss.
However, when face recognition system become able to compress well into feature template from face image more and more, leakage of face templates is more serious threat to user privacy. For example, face images can be reconstructed from face feature templates using neighborly de-convolutional neural network and this is serious threat to user privacy.
Blockchain
A number of third-party services require personal data, and users need to delegate personal data to service providers who may modify and share the data with other service providers.
For example, patients must share their medical records with hospitals, which can be updated and shared among different departments/hospitals and even insurance companies; internet users have to consent to personal data collection to use various services (e.g., location-based services, social media services), and personal data may be updated and shared for use in other inter-connected services.
Additionally, IoT devices in smart home systems exchange data with smart home hubs (e.g., Google Home, Amazon Alexa, Apple HomeKit). Even though such modification and sharing occur with the users’ consent, more transparency for the user is desired during the whole procedure.
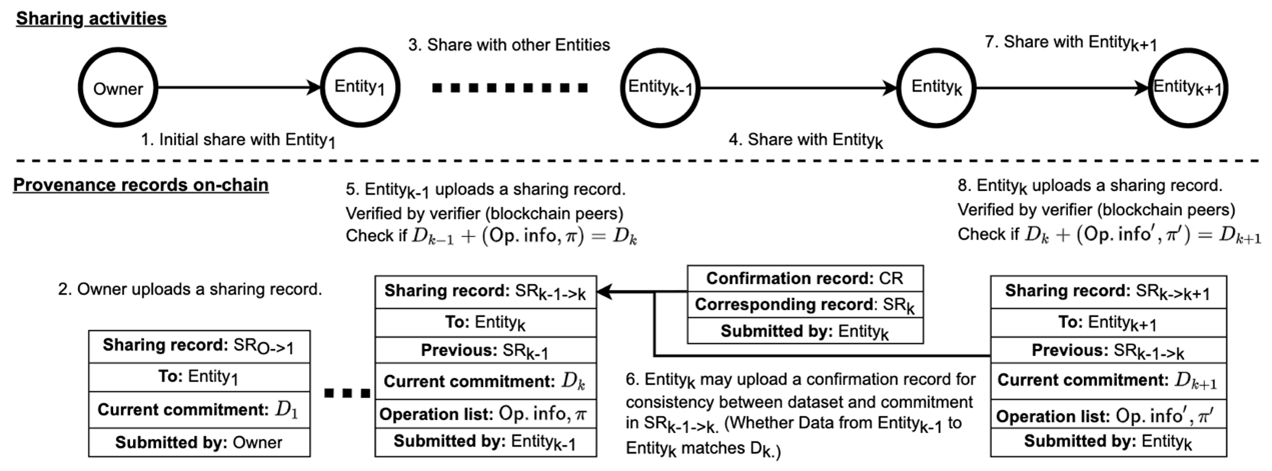
Personal data are shared by their owners with service providers for different needs, and these data can be modified and further shared among other service providers. For transparency and accountability of such delegated data, a personal data provenance monitoring system recording how owners’ data are propagated and modified is necessary.
However, achieving this involves significant challenges, due to the decentralized relationships of different service providers.
Therefore, we propose using blockchain to track the provenance of owners’ data.
While, for privacy reasons, what service providers can upload to the blockchain is limited to some sharing records that do not reveal data contents, and blockchain peers must validate them without actual data contents.
So, we propose a new extended vector commitment (EVC) scheme for monitoring personal data provenance in third-party services.
Functional Encryption
Functional Encryption (FE) is a new public key encryption system that extends the existing public key encryption concept more flexibly. It is a public key encryption that allows the decryption condition of a cipher text to be specified as an arbitrary function. At this time, Functional Encryption guarantees complete privacy by not exposing unnecessary information related to the cipher text to not only system outsiders but also system insiders.
The purpose of ongoing research (Research on Functional Encryption Technique Design, Analysis and Implementation Technology, supported by IITP) is to obtain the important source technologies of FE that is considered to be next-generation public-key encryption and to study the extended technologies of FE for cloud computing. In addition, this research studies techniques of other cryptographic primetives like Lattices.